Recent incidents involving renowned tech companies and cybersecurity firms highlight a critical reality: understanding security best practices for Microsoft 365 is not the same as effectively implementing them. But amid an epidemic of oversight, how do you close the gap between best practices and what’s really happening?
In this article:
The growing scale of the Microsoft 365 best practices challenge
It’s one thing to understand what Microsoft 365 best practices looks like and another to implement and enforce it consistently. In incidents like the Midnight Blizzard Microsoft hack, expertise alone didn't prevent organizations from falling prey to sophisticated cyberattacks. The only way to secure your Microsoft 365 environment is by making diligent security measures non-negotiable.
What can hacks like Midnight Blizzard tell us about the security of the average Microsoft 365 environment?
The weak links: unprotected accounts and human error
In one instance, a non-production test account lacking multi-factor authentication (2FA/MFA) was exploited. In another, a forgotten legacy account was compromised, demonstrating that human errors and oversights can lead to significant security breaches. These incidents serve as stark reminders that even low-risk accounts within Microsoft 365 can become vectors for security breaches if not adequately protected and monitored.
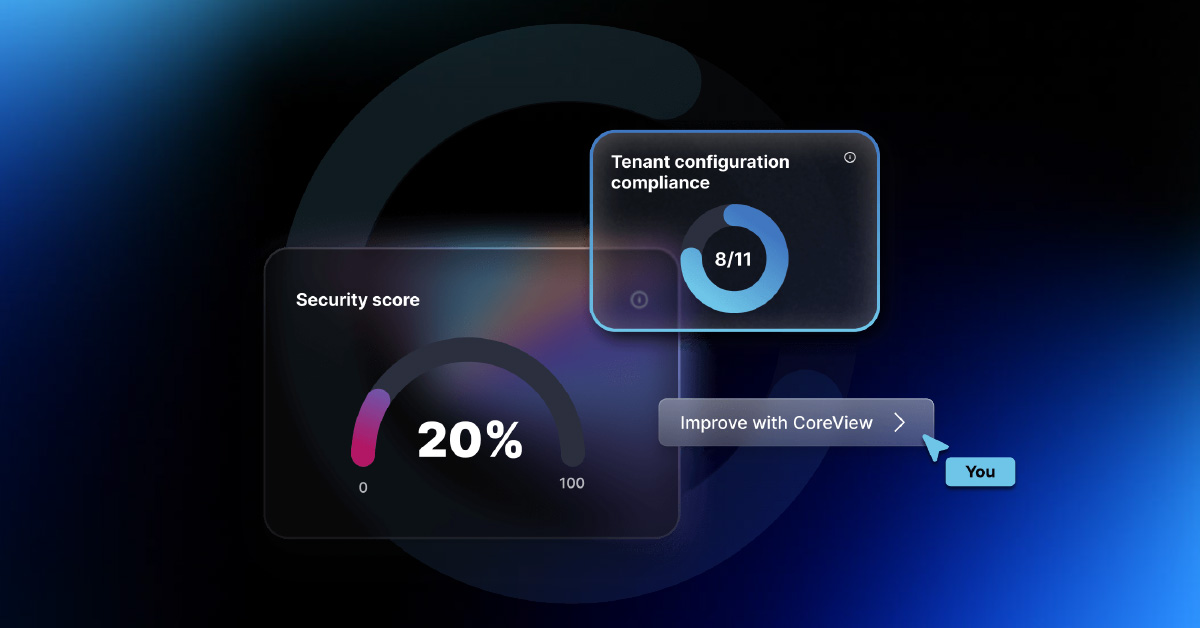
The oversight epidemic
The risk of seemingly innocuous accounts and the inevitability of human error can only be addressed with strong visibility across your Microsoft 365 environment. For many enterprises, this visibility is missing.
During a recent industry webinar, we were confronted with a startling revelation: 30% of IT professionals in attendance admitted the absence of a formalized process for reviewing Microsoft 365 user access within their organizations. This oversight isn’t just a minor gap; it's a gaping hole in the fabric of a company's security posture.
The evolution of digital threats
At the same time, the cybersecurity landscape is constantly evolving, particularly within the Microsoft 365 ecosystem. Digital threats are becoming increasingly sophisticated and the ripple effects of a single breach can impact multiple organizations. Consequently, the need for vigilance, proactive security management, and monitoring of Microsoft 365 is greater than ever. It’s not just your security at stake, but also your partners and supply chain.
Unchecked access: a prelude to chaos
Why is this mix of unprotected accounts, poor visibility, and evolving threats so alarming? Unchecked access can lead to catastrophic security breaches, regulatory non-compliance, and operational inefficiencies that can damage an organization's financial standing and reputation. The recent headlines speak for themselves: a tech leader being infiltrated by such a basic, brute-force hack reflects a fundamental, avoidable mistake with disastrous consequences.
How CoreView makes best practices more practical
At CoreView, we’ve distilled a decade of frontline experience into a robust suite of practices and tools designed to fortify your Microsoft 365 governance. We don't just preach best practices; those best practices are embedded into the fabric of your operations and make them simple to adopt and implement. With CoreView, you can close the gap between what your IT team already knows they should do and what they’re actually doing.
Our approach is built around seven key priorities:
- Implement and enforce multi-factor authentication (MFA): MFA isn’t a luxury, it's a necessity. It adds a critical layer of defense, ensuring that compromised credentials alone can’t grant access to your systems.
- Regularly review and update access permissions: Roles and responsibilities evolve; so should access permissions. Conduct periodic audits to ensure that only the right people have the right access at the right time.
- Eliminate legacy accounts and reduce attack surfaces: Old, unused accounts are open invitations to cybercriminals. Identify and decommission such accounts to minimize vulnerabilities.
- Educate and empower your workforce: Humans are your first line of defense. Regular training on cybersecurity best practices can transform your workforce from a potential liability into a formidable barrier against threats.
- Leverage advanced threat protection tools: Use sophisticated tools that offer real-time threat detection, automated alerts, and actionable insights to stay ahead of potential threats.
- Embrace a zero trust security model: Adopt a 'never trust, always verify' stance. Zero trust ensures meticulous identity verification for anyone trying to access resources in your network, regardless of where they’re accessing from.
- Ensure compliance through continuous monitoring: Regulatory landscapes are dynamic. Implement continuous monitoring mechanisms to ensure ongoing compliance and swiftly adapt to new regulations.
At CoreView, we ensure that best practices are more than just understood—they’re effectively implemented and continuously monitored. Our focus on vigilance enables quick threat detection and response, protecting your Microsoft 365 assets over the long term.
Our promise to you
With CoreView, you're not alone in securing your Microsoft 365 environment. We stand with you, applying a decade of experience to defend against today's threats and those on the horizon. Together, we'll strengthen your defenses and secure your digital landscape.