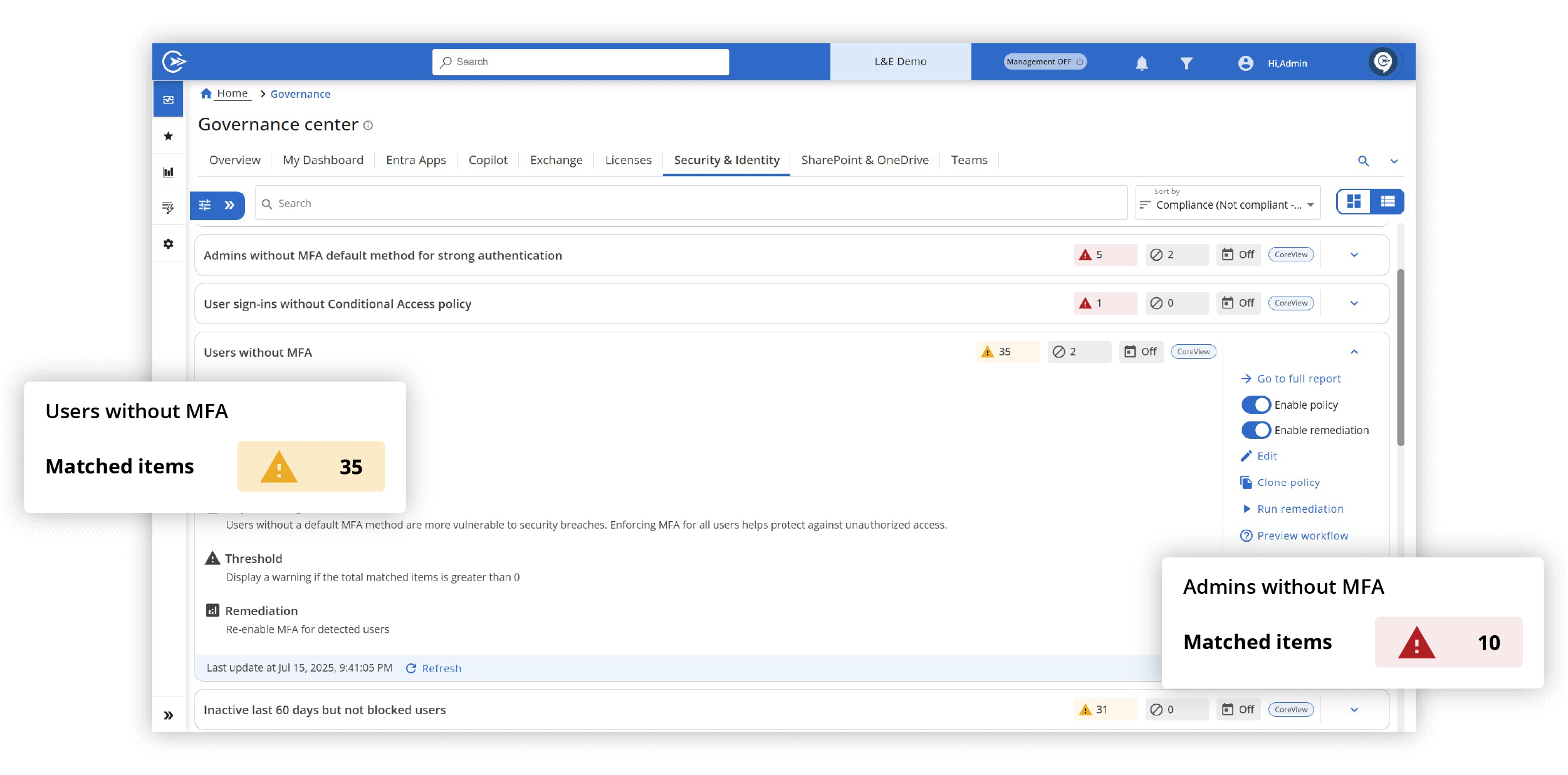
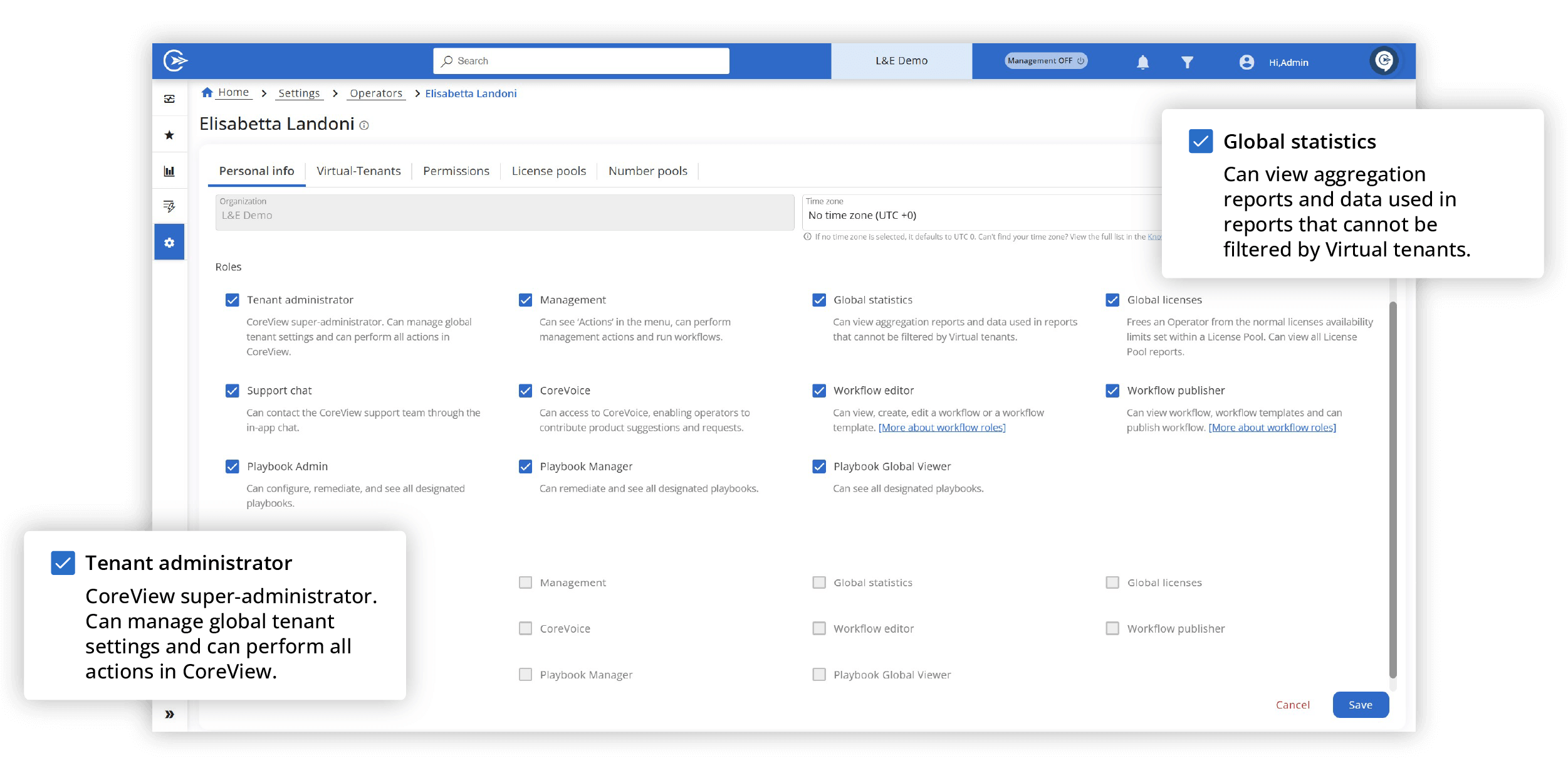
The legacy approach to Microsoft security isn’t fit for purpose
Microsoft 365 tenants face growing attacks, but legacy tools can’t keep up. Microsoft 365 and Entra lack essentials like configuration backup, drift detection, least privilege segmentation, secure collaboration, and strong zero trust enforcement. It’s time for a new approach.